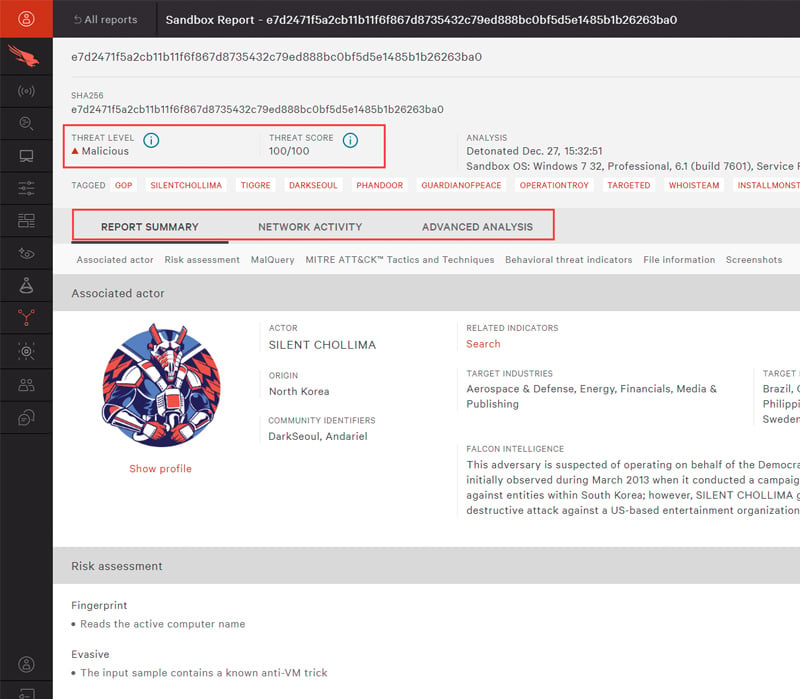
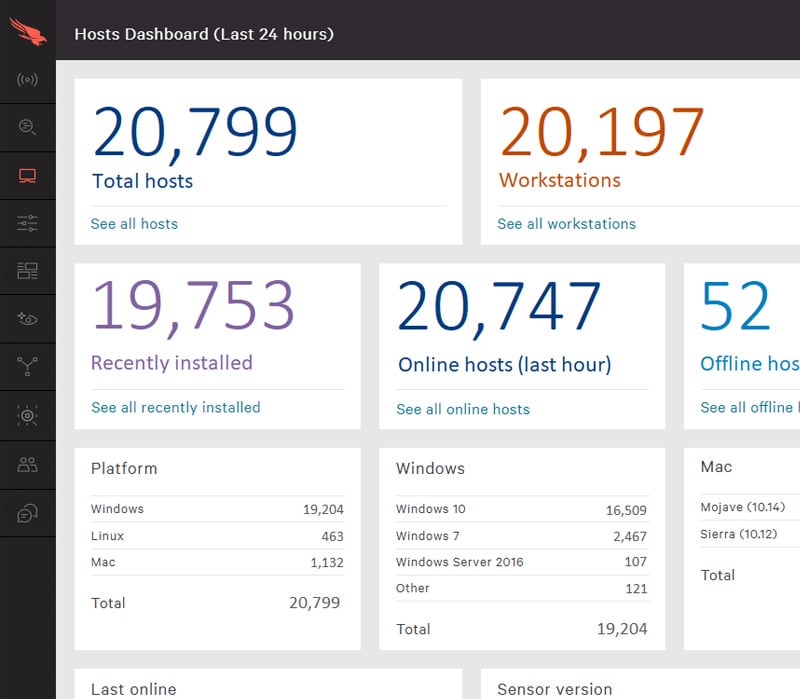
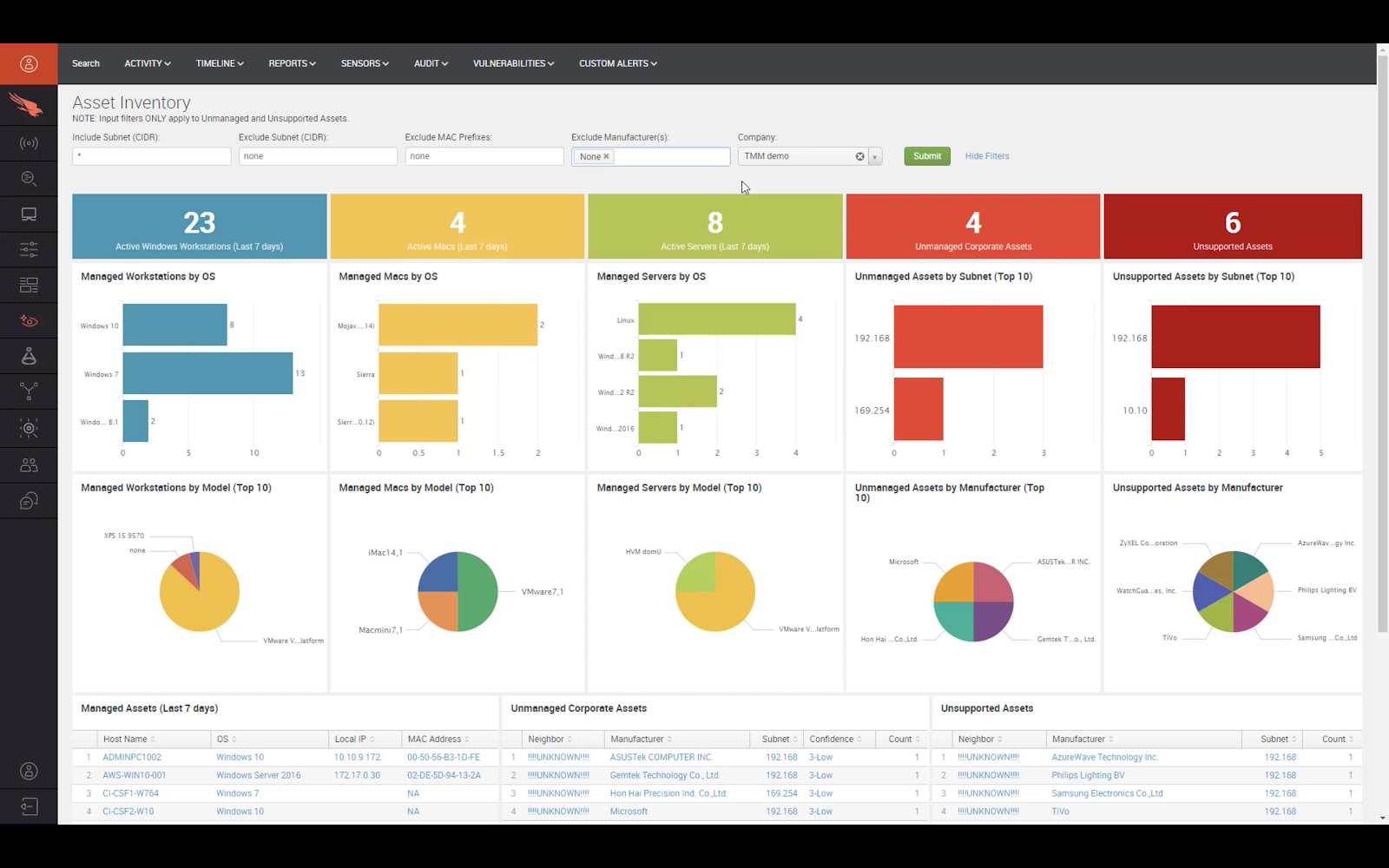
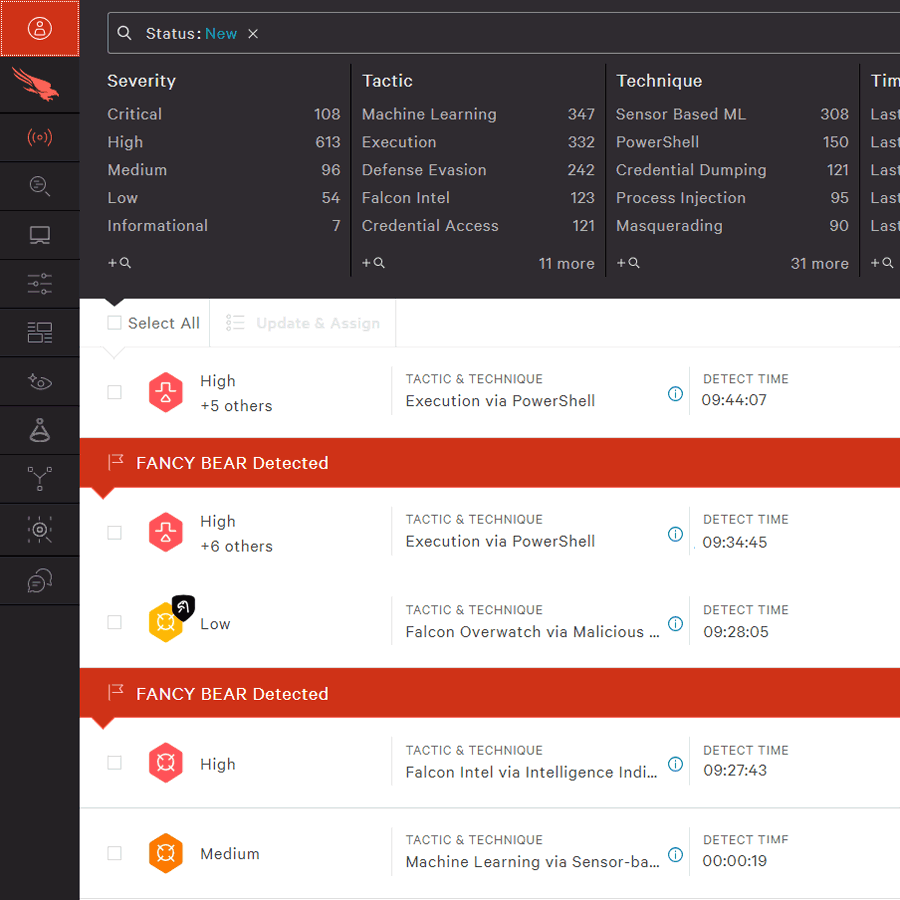
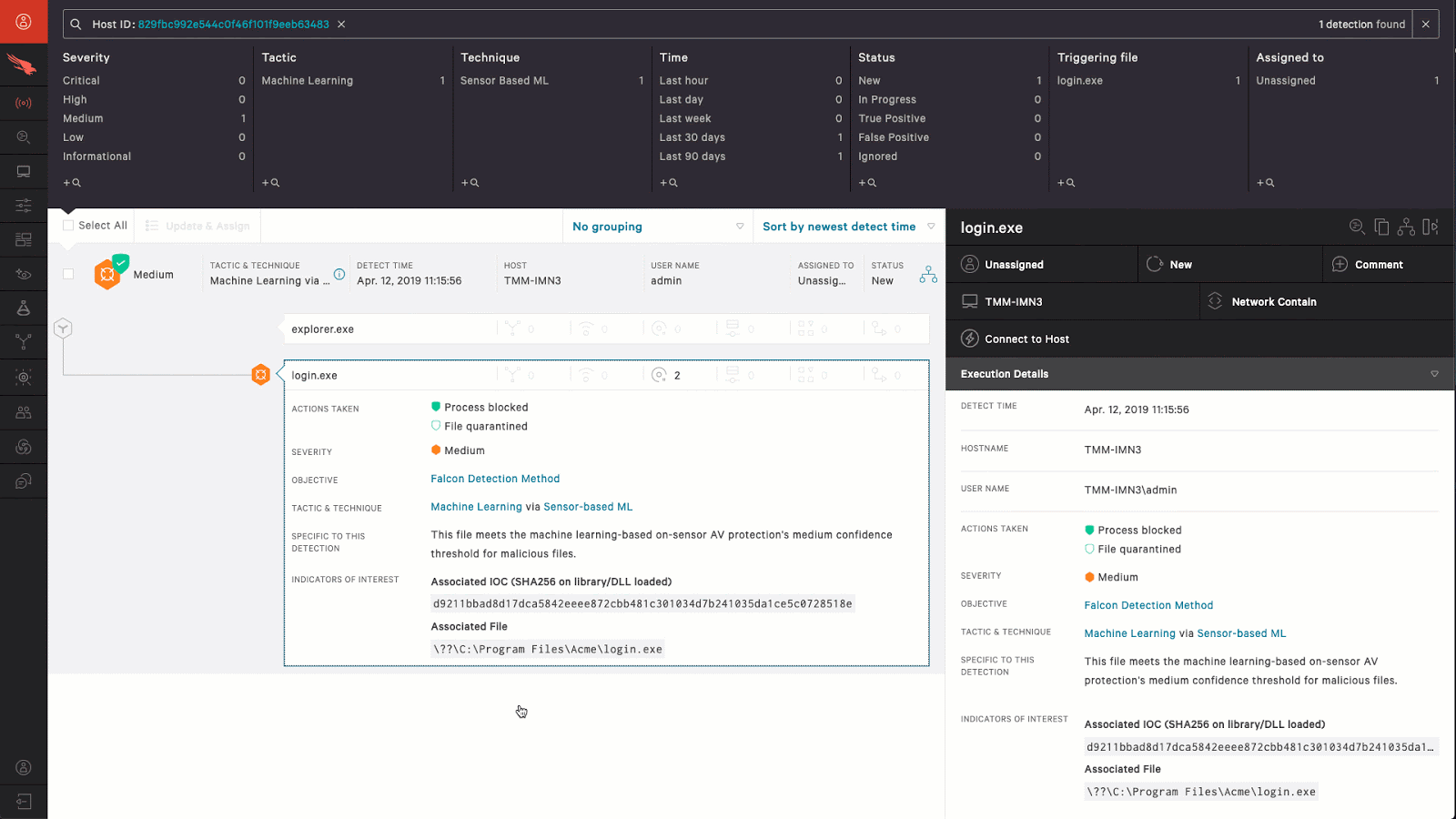
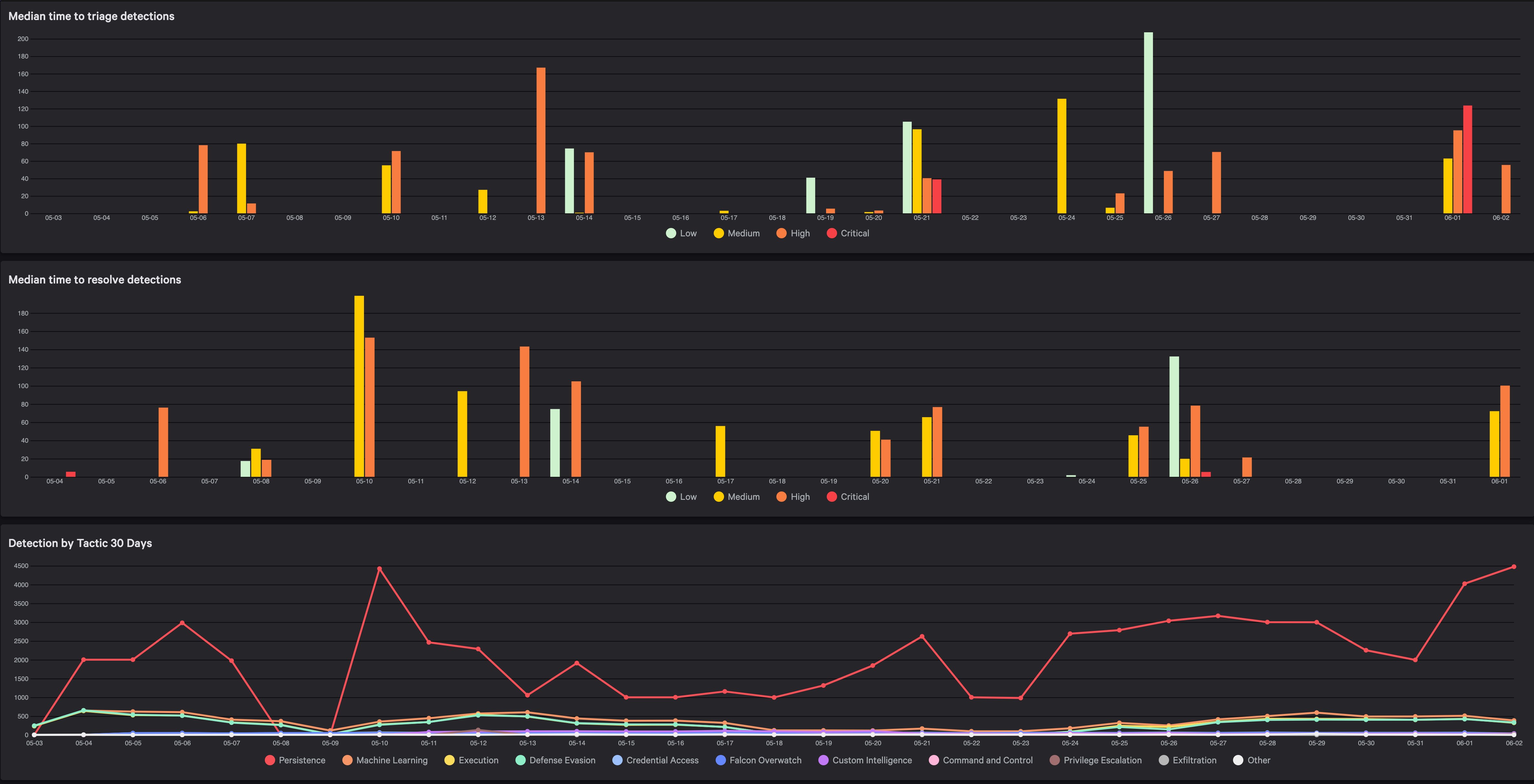
Что такое crowdstrike falcon
Falcon Identity Threat Detection
Falcon Identity Threat Detection (ITD) enables hyper-accurate detection of identity-based threats in real-time, leveraging AI and behaviorial analytics to provide deep actionable insights to stop modern attacks like ransomware.
Request a Demo
Know what accounts are doing before breaches happen
Insights & Analytics for All Credentials
Falcon ITD lets you see all Service and Privileged accounts on your network and cloud with full credential profiles and weak authentication discovery across every domain. Analyze every domain in your organization for potential vulnerability from stale credentials, weak or stale passwords, see all service connections and weak authentication protocols in use.
Detect lateral movement for authenticated accounts
Falcon ITD monitors the domain controllers on premises or in the cloud (via API) to see all authentication traffic. Falcon ITD creates a baseline for all entities and compares behavior against unusual lateral movement, Golden Ticket attacks, Mimikatz traffic patterns and other related threats. Falcon ITD can help you see Escalation of Privilege and anomalous Service Account activity.
AD Security without using logs
Falcon ITD reduces time to detect by viewing live authentication traffic, which expedites finding and resolving incidents. See real-time events and potential incidents during authentication by rogue users of any type. Falcon ITD offers curated traffic feeds to enrich the «what» of identity protection events with the «who» of credential identification.
FALCON ENDPOINT
PROTECTION PRO
Market-leading NGAV proven to stop malware with integrated threat intelligence and immediate response — with a single lightweight agent that operates without the need for constant signature updates, on-premises management infrastructure or complex integrations, making it fast and easy to replace your AV.
FALCON
PREVENT Next-Generation
Antivirus
FALCON X Threat Intelligence
FALCON
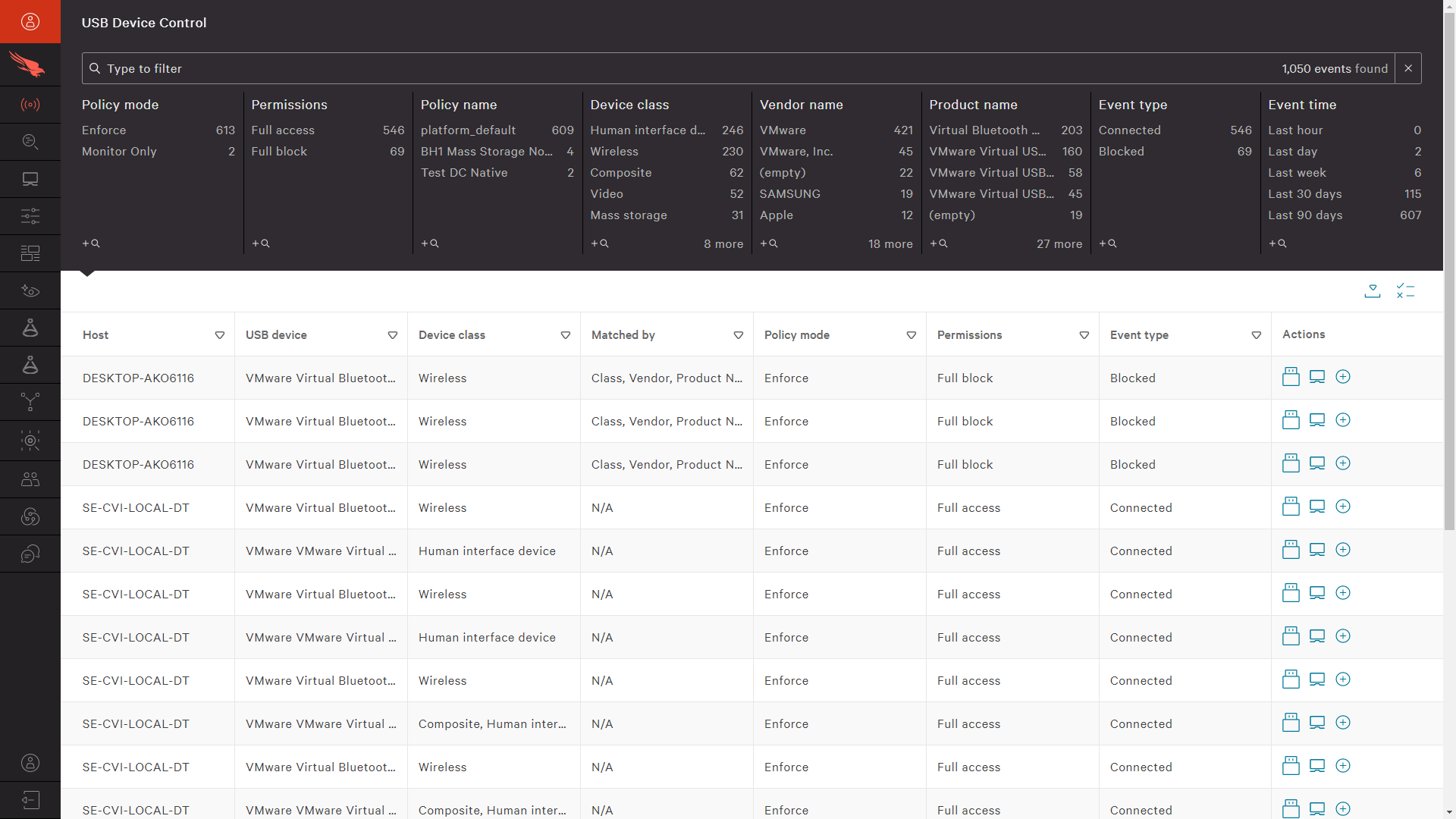
Device Control USB Device Control
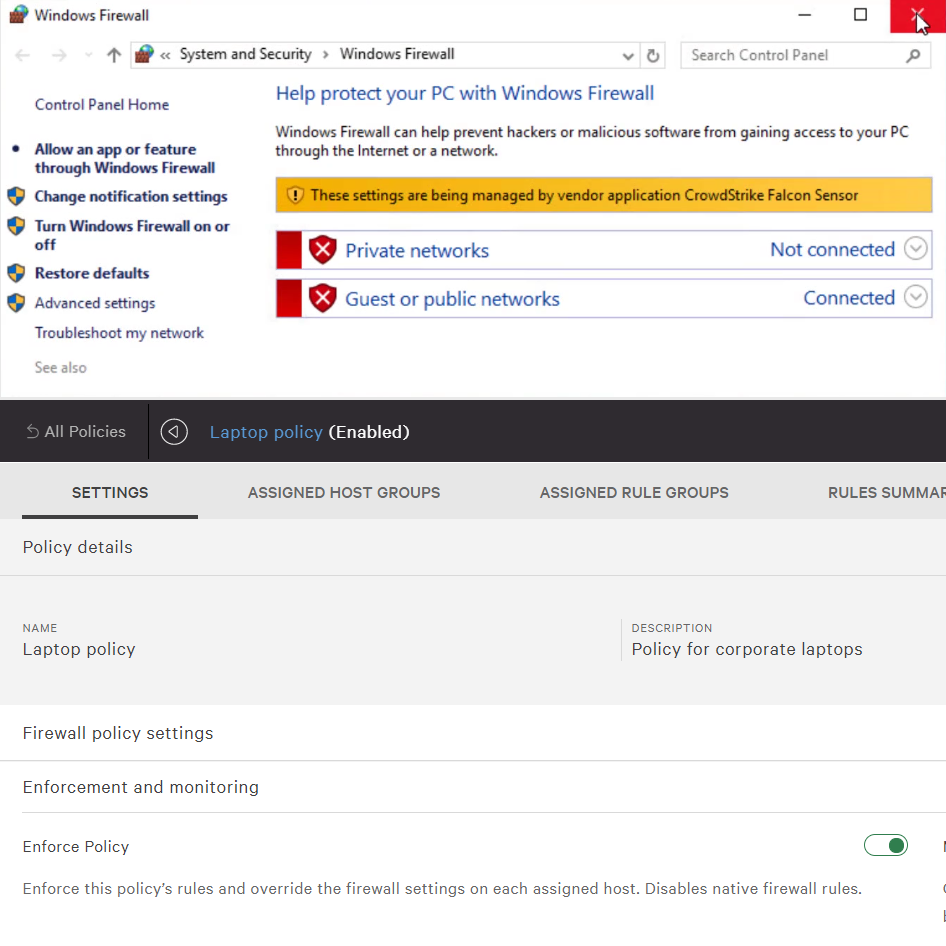
Falcon Firewall Management Host Firewall Control
FALCON
INSIGHT Endpoint Detection
& Response
FALCON
OVERWATCH Threat Hunting
FALCON
DISCOVER IT Hygiene
CROWDSTRIKE
SERVICES Incident Response &
Proactive Services
Recognized by Gartner Peer Insights CrowdStrike named a Customers’ Choice vendor in the 2021 Gartner Peer Insights Report for EPP. Learn More.
NEXT-GEN AV SOLUTION:
ENDPOINT PROTECTION PRO
Falcon Endpoint Protection Pro offers the ideal AV replacement solution by combining the most effective prevention technologies and full attack visibility with built-in threat intelligence — all in a single lightweight agent.
BUSINESS VALUE
We don’t have an antivirus solution that’s waiting on signatures to be developed and pushed out. What we’ve got is that we’re part of a larger collection of organizations that are running CrowdStrike, so any data that we see gets fed back into the system and someone else will benefit from that knowledge. And it’s all because it is cloud-based.
MODULES INCLUDE
Protects against both malware and malware-free attacks; third-party tested and certified, allowing organizations to confidently replace their existing legacy AV
Integrates threat intelligence into endpoint protection, automating incident investigations and speeding breach response
Enable safe and accountable USB device usage with effortless visibility and precise and granular control of USB device utilization
Provides simple, centralized firewall management, making it easy to manage and enforce host firewall policies
Compare CrowdStrike
See how CrowdStrike stacks up against the competition.
What is CrowdStrike? Falcon Platform FAQ
Want to see the CrowdStrike Falcon platform in action? Start with a free trial of next-gen antivirus:
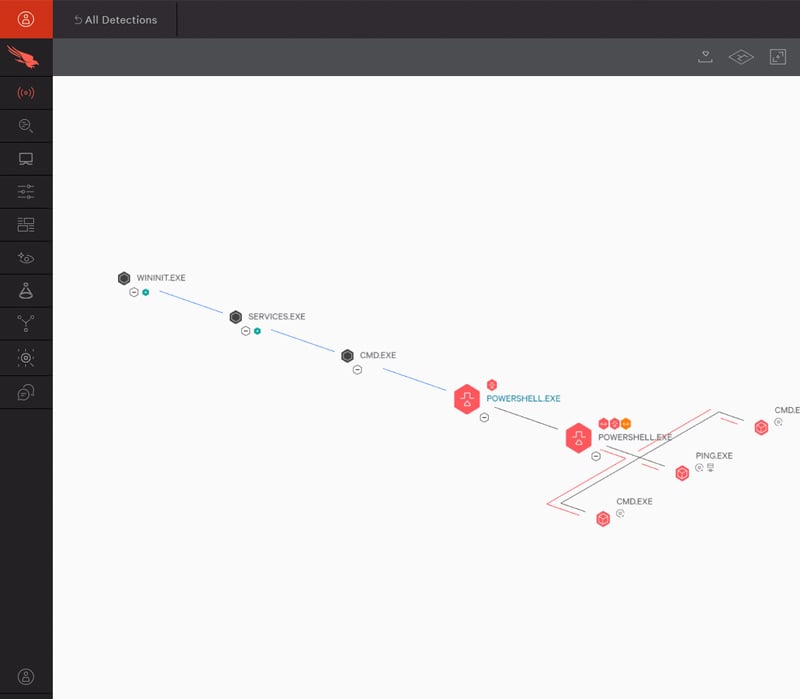
Falcon is the CrowdStrike platform purpose-built to stop breaches via a unified set of cloud-delivered technologies that prevent all types of attacks — including malware and much more. Today’s sophisticated attackers are going “beyond malware” to breach organizations, increasingly relying on exploits, zero days, and hard-to-detect methods such as credential theft and tools that are already part of the victim’s environment or operating system, such as PowerShell. CrowdStrike Falcon responds to those challenges with a powerful yet lightweight solution that unifies next-generation antivirus (NGAV), endpoint detection and response (EDR), cyber threat intelligence,managed threat hunting capabilities and security hygiene — all contained in a tiny, single, lightweight sensor that is cloud-managed and delivered.
The CrowdStrike Falcon Platform includes:
Endpoint Security Solutions
Security & IT Operations
Cloud Security Solutions
Identity Protection Solutions
Falcon Fusion is a unified and extensible SOAR framework, integrated with Falcon Endpoint and Cloud Protection solutions, to orchestrate and automate any complex workflows. Fusion leverages the power of the Security Cloud and relevant contextual insights across endpoints, identities, workloads, in addition to telemetry from partner applications to ensure effective workflow automation.
Falcon Prevent or Falcon Insight.
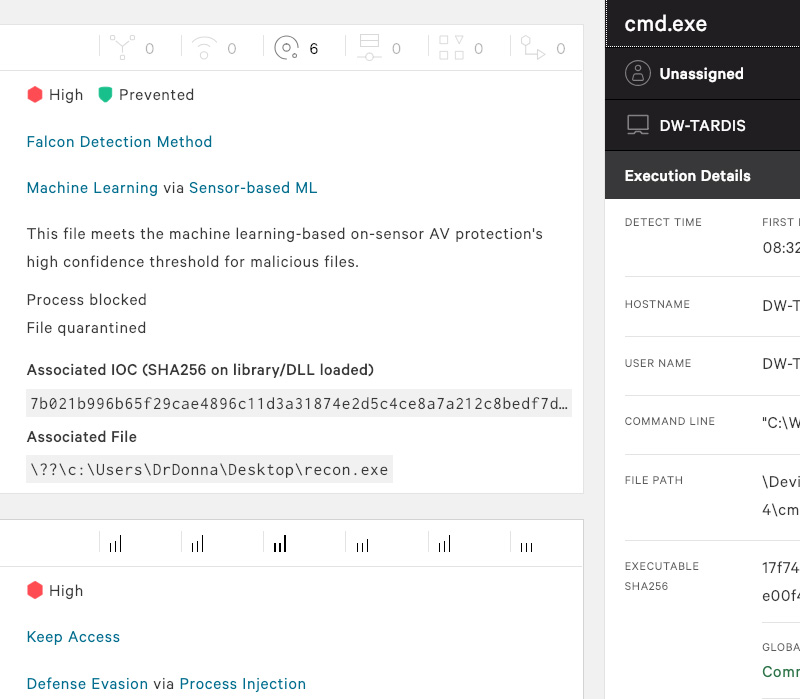
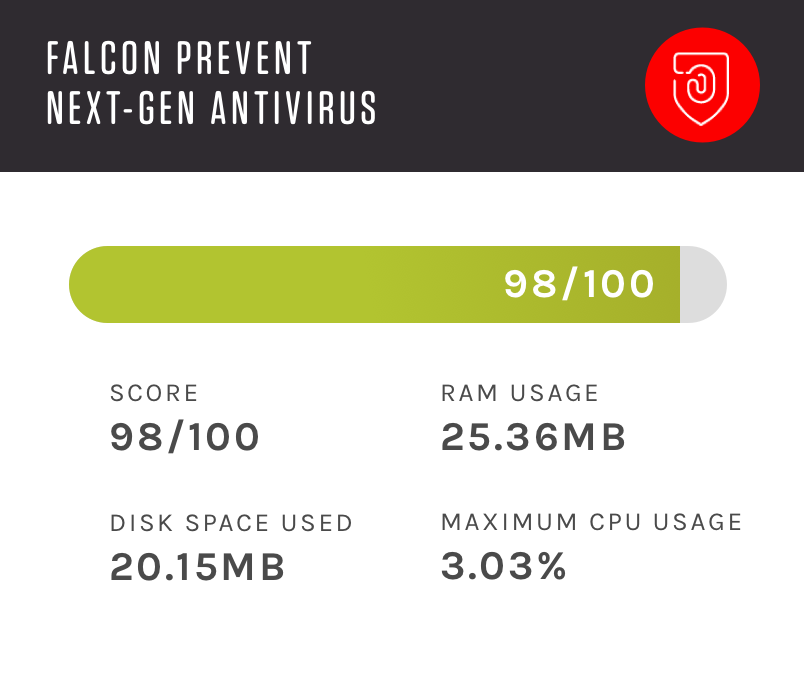
Falcon Prevent provides next generation antivirus (NGAV) capabilities, delivering comprehensive and proven protection to defend your organization against both malware and malware-free attacks. Incorporating identification of known malware, machine learning for unknown malware, exploit blocking and advanced Indicator of Attack (IOA) behavioral techniques, CrowdStrike Falcon Prevent allows organizations to confidently replace their existing legacy AV solutions.
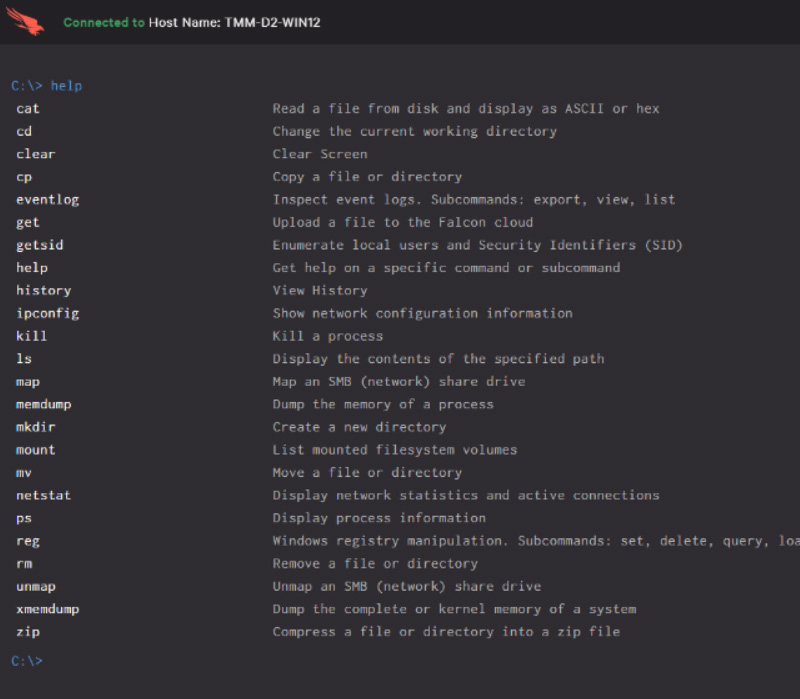
Falcon Insight provides endpoint detection and response (EDR) capabilities, allowing for continuous and comprehensive visibility to tell you what’s happening on your endpoints in real time. The extensive capabilities of Falcon Insight span across detection, response and forensics, to ensure nothing is missed, so potential breaches can be stopped before your operations are compromised.
Falcon OverWatch is a managed threat hunting solution. To defeat sophisticated adversaries focused on breaching your organization, you need a dedicated team working for you 24/7 to proactively identify attacks. The global Falcon OverWatch team seamlessly augments your in-house security resources to pinpoint malicious activities at the earliest possible stage, stopping adversaries in their tracks.
Falcon Discover is an IT hygiene solution that identifies unauthorized systems and applications, and monitors the use of privileged user accounts anywhere in your environment — all in real time, enabling remediation as needed to improve your overall security posture.
Yes, CrowdStrike Falcon Prevent allows organizations to confidently replace their existing legacy AV solutions. Incorporating identification and prevention of known malware, machine learning for unknown malware, exploit blocking and advanced Indicator of Attack (IOA) behavioral techniques, Falcon Prevent protects against attacks whether your endpoints are online or offline. Falcon Prevent also features integration with Windows System Center, for those organizations who need to prove compliance with appropriate regulatory requirements.
Yes, CrowdStrike Falcon has been certified by independent third parties as an AV replacement solution.
The extensive capabilities of CrowdStrike Falcon allows customers to consider replacing existing products and capabilities that they may already have, such as:
Yes, CrowdStrike Falcon can help organizations in their efforts to meet numerous compliance and certification requirements. Falcon has received third-party validation for the following regulations: PCI DSS v3.2 | HIPAA | NIST | FFIEC | PCI Forensics | NSA-CIRA | SOC 2 | CSA-STAR | AMTSO | AV Comparatives.
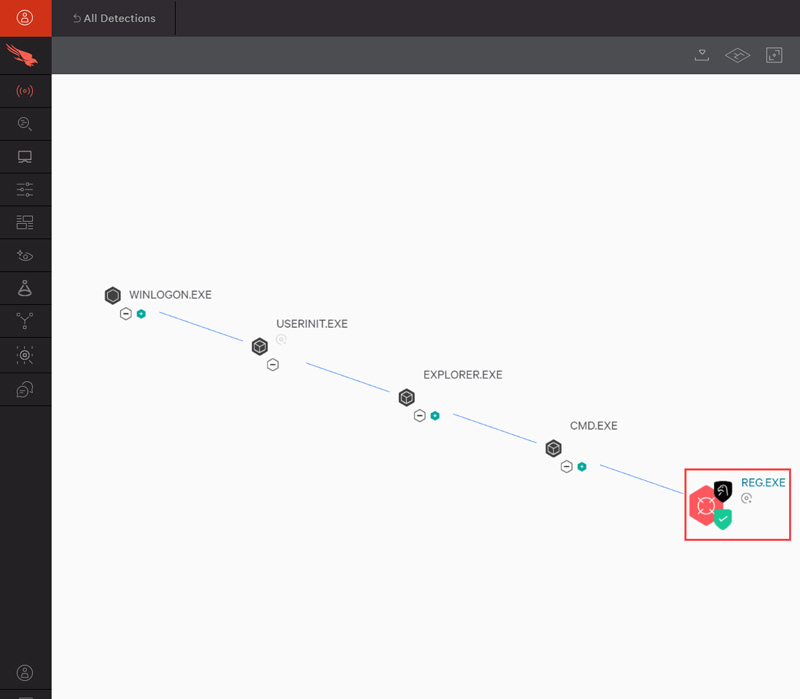
CrowdStrike is the pioneer of cloud-delivered endpoint protection. CrowdStrike Falcon has revolutionized endpoint security by being the first and only solution to unify next-generation antivirus, endpoint detection and response (EDR), and a 24/7 threat hunting service — all delivered via a single lightweight agent. Using its purpose-built cloud native architecture, CrowdStrike collects and analyzes more than 30 billion endpoint events per day from millions of sensors deployed across 176 countries. The unique benefits of this unified and lightweight approach include immediate time-to-value, better performance, reduced cost and complexity, and better protection that goes beyond detecting malware to stop breaches before they occur. These capabilities are based on a unique combination of prevention technologies such as machine learning, Indicators of Attack (IOA), exploit blocking, unparalleled real-time visibility and 24×7 managed hunting to discover and track even the stealthiest attackers before they do damage.
Absolutely, CrowdStrike Falcon is used extensively for incident response. Falcon Insight provides remote visibility across endpoints throughout the environment, enabling instant access to the “who, what, when, where and how” of an attack. The cloud-based architecture of Falcon Insight enables significantly faster incident response and remediation times.
Yes, Falcon Prevent offers powerful and comprehensive prevention capabilities. Falcon Prevent can stop execution of malicious code, block zero-day exploits, kill processes and contain command and control callbacks.
Yes, indeed, the lightweight Falcon sensor that runs on each endpoint includes all the prevention technologies required to protect the endpoint, whether it is online or offline. Those technologies include machine learning to protect against known and zero-day malware, exploit blocking, hash blocking and CrowdStrike’s behavioral artificial intelligence heuristic algorithms, known as Indicators of Attack (IOAs).
No, CrowdStrike Falcon delivers next-generation endpoint protection software via the cloud. A key element of “next gen” is reducing overhead, friction and cost in protecting your environment. There is no on-premises equipment to be maintained, managed or updated. The Falcon sensor is unobtrusive in terms of endpoint system resources and updates are seamless, requiring no re-boots. The Falcon web-based management console provides an intuitive and informative view of your complete environment.
No, Falcon was designed to interoperate without obstructing other endpoint security solutions, including third-party AV and malware detection systems.
Falcon Connect has been created to fully leverage the power of Falcon Platform. Falcon Connect provides the APIs, resources and tools needed by customers and partners to develop, integrate and extend the use of the Falcon Platform itself, and to provide interoperability with other security platforms and tools. Find out more about the Falcon APIs: Falcon Connect and APIs.
Yes, Falcon offers two points of integration with SIEM solutions:
Literally minutes — a single lightweight sensor is deployed to your endpoints as you monitor and manage your environment via a web console. With CrowdStrike Falcon there are no controllers to be installed, configured, updated or maintained: there is no on-premises equipment.
The Falcon sensor’s design makes it extremely lightweight (consuming 1% or less of CPU) and unobtrusive: there’s no UI, no pop-ups, no reboots, and all updates are performed silently and automatically.
64-bit Desktop OSes:
32-bit Desktop OSes:
We support these x86_64 versions of these Linux server OSes:
Docker is also supported. See Deployment Guide for details.
These are the supported MacOS:
Yes, Falcon is a proven cloud-based platform enabling customers to scale seamlessly and with no performance impact across large environments. The platform’s “frictionless” deployment has been successfully verified across enterprise environments containing more than 100,000 endpoints.
CrowdStrike Falcon is a 100 percent cloud-based solution, offering Security as a Service (SaaS) to customers. Falcon requires no servers or controllers to be installed, freeing you from the cost and hassle of managing, maintaining and updating on-premises software or equipment.
Yes, CrowdStrike’s US commercial cloud is compliant with Service Organization Control 2 standards and provides its Falcon customers with an SOC 2®️ report. Additional information on CrowdStrike certifications can be found on our Compliance and Certifications page.
All data transmitted from the sensor to the cloud is protected in an SSL/TLS-encrypted tunnel. On average, each sensor transmits about 5-8 MBs/day.
CrowdStrike Falcon is designed to maximize customer visibility into real-time and historical endpoint security events by gathering event data needed to identify, understand and respond to attacks — but nothing more. This default set of system events focused on process execution is continually monitored for suspicious activity. When such activity is detected, additional data collection activities are initiated to better understand the situation and enable a timely response to the event, as needed or desired. Note that the specific data collected changes as we advance our capabilities and in response to changes in the threat landscape. Information related to activity on the endpoint is gathered via the Falcon sensor and made available to the customer via the secure Falcon web management console.
Yes, CrowdStrike recognizes that organizations must meet a wide range of compliance and policy requirements. In order to meet the needs of all types of organizations, CrowdStrike offers customers multiple data residency options. Contact CrowdStrike for more information about which cloud is best for your organization.
All data sent from the CrowdStrike Falcon sensor is tagged with unique, anonymous identifier values. Data and identifiers are always stored separately. Once in our cloud, the data is heavily protected with strict data privacy and access control policies. All data access within the system is managed through constrained APIs that require a customer-specific token to access only that customer’s data. Our analysis engines act on the raw event data, and only leverage the anonymized identifier values for clustering of results.
While other security solutions rely solely on Indicators of Compromise (IOCs) — such as known malware signatures, hashes, domains, IPs and other clues left behind after a breach — CrowdStrike also can detect live Indicators of Attack (IOAs), identifying adversarial activity and behaviors across the entire attack timeline, all in real time. Falcon’s unique ability to detect IOAs allows you to stop attacks
For known threats, Falcon provides cloud-based antivirus and IOC detection capabilities. For unknown and zero-day threats, Falcon applies IOA detection, using machine learning techniques to build predictive models that can detect never-before-seen malicious activities with high accuracy. Driven by the CrowdStrike Threat Graph™ data model, this IOA analysis recognizes behavioral patterns to detect new attacks, whether they use malware or not. The range and capability of Falcon’s detection techniques far surpass other security solutions on the market, particularly with regard to unknown and previously undetectable emerging threats.
Falcon Prevent stops known and unknown malware by using an array of complementary methods:
Customers can control and configure all of the prevention capabilities of Falcon within the configuration interface.
Yes, Falcon includes a feature called the Machine Learning Slider, that offers several options to control thresholds for machine learning. In addition, this unique feature allows users to set up independent thresholds for detection and prevention.
Falcon Prevent uses an array of complementary prevention and detection methods to protect against ransomware:
CrowdStrike Falcon is equally effective against attacks occurring on-disk or in-memory. The platform continuously watches for suspicious processes, events and activities, wherever they may occur.
Falcon X Recon: Digital Risk Protection
CrowdStrike Falcon X Reconв„ў monitors potentially malicious activity across the open, deep and dark web to enable organizations to better protect their brand, employees and sensitive data.
Attend Free Hands-on Workshop
Falcon X Recon Offerings
CHOOSE THE OPTION THAT SUITS YOU BEST
Falcon X Recon enables security teams to monitor and track adversaries across the open, deep and dark web.
Includes everything in Falcon X Recon, but CrowdStrike manages it for you. Falcon X Recon+ reduces the time, skills and effort required for you to battle sophisticated adversaries.
| Falcon X Recon | Falcon X Recon+ | |
|---|---|---|
| Access Data from the Open, Deep, and Dark Web | ||
| Create Monitoring Rules | ||
| Set and Manage Alerts | ||
| Universal Search | ||
| Actor Profiles and Indicator Feed | ||
| Assigned CrowdStrike Expert | ||
| Managed rule monitoring | ||
| Alert triage and assessment | ||
| Mitigation recommendations | ||
| Updates and threat briefings | ||
| Takedown Service |
GAIN SITUATIONAL AWARENESS ACROSS THE DARK WEB AND BEYOND
Falcon X Recon exposes digital risk by monitoring the hidden recesses of the internet where criminal actors congregate and underground economies thrive.
Falcon X Recon provides real-time visibility to potential threats, reducing investigation time and improving efficiency and response.
Take immediate action against digital risk on Day One — Falcon X Recon is built on the cloud-native CrowdStrike Falcon® platform so there’s nothing to install, administer or deploy.
Falcon Complete:
Managed Detection and Response (MDR)
Falcon Complete stops breaches every hour of every day, through expert management, threat hunting, monitoring and remediation, and is backed by CrowdStrike’s Breach Prevention Warranty.
Watch Demo
CrowdStrike named a Leader
IDC MarketScape: US MDR Services 2021 Vendor Assessment Recognized by Industry Experts as a Leader In Managed Detection and Response Forrester Waveв„ў: Managed Detection and Response, Q1 2021 Read the report to learn the key capabilities Forrester recommends that organizations demand when looking for an MDR provider.
Why Choose Falcon Complete for Managed Detection and Response?
Augment your Team with the Deepest Expertise
Cybersecurity is not just a technology problem, it also requires around-the-clock expertise.
Falcon Complete brings you focused expertise to stop threats through continuous vigilance.
PROTECTION 24/7/365
Eradicate Threats in Minutes
Adversaries often inflict damage in hours, but it can take days for organizations to respond.
Falcon Complete surgically eliminates threats in minutes.
Forrester Study Finds Falcon Complete Delivers
403% ROI,
100% Confidence
Learn more in the Total Economic Impactв„ў (TEI) of CrowdStrike Falcon Complete, a commissioned study conducted by Forrester Consulting on behalf of CrowdStrike.
Falcon Complete Features
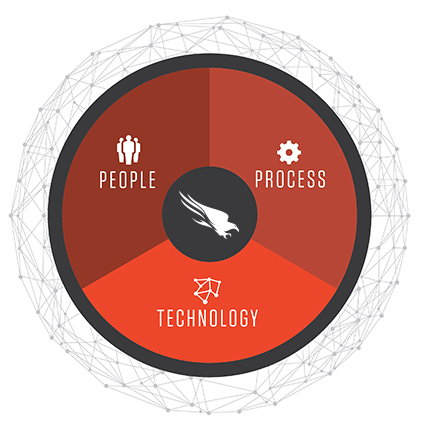
People, Process and Technology Are All Key to Stopping Breaches
Layers of Expertise
The Falcon Complete team is composed of seasoned security professionals who have experience in incident handling, incident response, forensics, SOC analysis and IT administration. The team has a global footprint, allowing true 24/7 “follow the sun” coverage.
Powered by the Falcon Platform
CrowdStrike pioneered a new approach to endpoint and cloud workload protection, designed and built to overcome the limitations of legacy security solutions. The Falcon platform delivers the foundation for true next-generation protection.
Proactive Management and Optimization
CrowdStrike experts ensure your environment is continuously optimized to combat the latest threats, achieving the best levels of performance and protection from your Falcon investment and ensuring confidence that your endpoint protection is always under complete control.
Continuous Human Threat Hunting
Falcon Complete includes 24/7 monitoring by the Falcon OverWatch team, CrowdStrike’s human threat detection engine that hunts relentlessly to see and stop the most sophisticated hidden threats.
24/7 Monitoring and Response
The Falcon Complete team monitors your Falcon platform 24 hours a day, seven days a week, investigating every security alert with the goal of identifying potential intrusions at their very earliest stages.
Surgical Remediation
When an intrusion is identified, the team acts quickly and decisively. The team remotely accesses the affected system using native Falcon capabilities to surgically remove persistence mechanisms, stop active processes and clear other latent artifacts. Falcon Complete restores systems to their pre-intrusion state without the burden and disruption of reimaging systems.
Transparent and Secure Collaboration
Falcon Complete delivers simple, transparent visibility and collaboration with CrowdStrike’s analysts ensuring you always have the information you need to make fast and effective decisions.
Breach Prevention Warranty
CrowdStrike stands strongly behind its breach protection capabilities. Falcon Complete comes with a Breach Prevention Warranty* to cover costs should a breach occur within the protected environment.
Components of Falcon Complete
Struggling to protect cloud workloads?
Falcon Cloud Workload Protection (CWP) Complete provides managed protection for workloads and containers, enabling you to build, run, and secure applications with speed and confidence.
Falcon Complete vs. Other MDR
The Falcon Complete Difference
Falcon Complete MDR
Falcon Complete stops breaches with our balanced combination of technology, expertise, and discipline, backed with our industry-leading Breach Prevention Warranty.
Competing solutions monitor and provide guidance as a “best effort”, but the responsibility and work to manage and respond to threats remains with your team.
Customer Recognition
“Security Footprint Of A Fortune 500 With The Security Staff Of A Startup”
“What I like most is having peace of mind when it comes to our company’s security. We have the security staff of a small startup with the security footprint of a Fortune 500.” – Tech Ops Manager, Industry: Services
“Falcon Is Peerless In The NGAV/EDR/MDR Space”
“CrowdStrike exemplifies their values and puts in the extra effort to ensure they are exceeding our needs. Deployment is stupid easy, management is seamless, and opting for the Complete service is like a warm blanket on a cold night.” – Information Security Manager, Industry: Manufacturing
“Gartner Peer Insights: Best In Class Service”
“We wanted to adopt best-in-class cybersecurity protection without incurring the expense of building out an internal cybersecurity team.” – Systems Engineer, Industry: Finance
The GARTNER PEER INSIGHTS Logo is a trademark and service mark of Gartner, Inc. and/or its affiliates and is used herein with permission. All rights reserved. Gartner Peer Insights reviews constitute the subjective opinions of individual end users based on their own experiences and do not represent the views of Gartner or its affiliates.